5G Network Slicing and Security
Emmanuel Dotaro, Head of ICT and Security Labs at Thales Secure Communications and Information Systems – France
IEEE Softwarization, January 2018
5G network slicing comes with Security Transformation Requirements
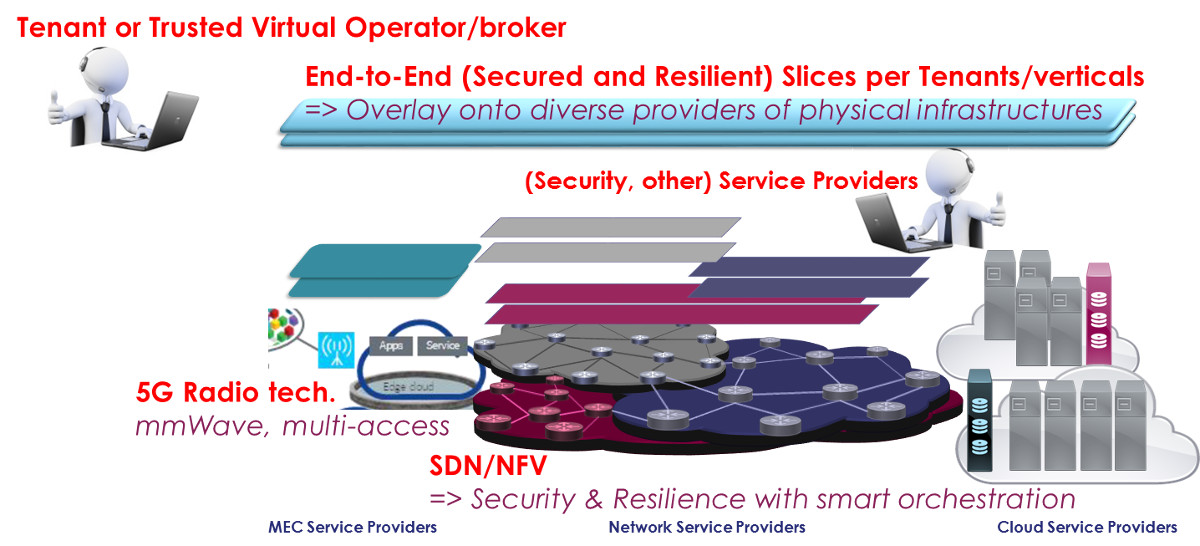
Despite the lack of common understanding or unique standard definition, the network slicing concept has been used with the same virtualization fundamentals in many contexts. From the GENI concept [1], in MPLS/GMPLS framework [2] towards 5G [3], most of the visions consider a set of resources virtualized for the benefit of a tenant, sharing de-facto part of the control/management with the underlying infrastructure. The immediate security issue was related to the isolation between slices but already in [4] NGMN listed a set of key security issues beyond basic isolation concerns. The overall slice vision is illustrated in Fig. 1
The 5G slicing security is one security area among many 5G other specific issues. 5G (beyond 3GPP phase 1) will encompass non-3GPP domains, extended roaming procedures, Service Based Architecture (SAB) applied to security and will certainly bring unprecedented architectures, services or business models. The evolution towards the next generation has already been subject to a substantial literature. Considering the 5G architecture and procedures introduced in [5] and [6], security areas are more specifically addressed in [7][8]. Going far beyond 4G complexity, 5G is imposing to reconsider many security aspects such as Authentication and Authorization, RAN (multi-access) security, User Equipment (including IoT), confidentiality and key management, etc...and finally Network Slicing security. An overall vision of this security landscape is given in [9] where one can find references to groups and bodies active on 5G security such as ETSI --in particular working groups dealing with Network Function Virtualization (NFV) and management issues (MANO), IETF, IMT 2020,...
The nature of 5G components, systems and services lead to an unprecedented combination of specific software-based vulnerabilities, function distribution, boundaries variations in time and space.
Moreover, the multiplicity of stakeholders and authorities in the case of Network slicing raises serious challenges which are exacerbated by the so-called Mission-Critical support.
Through technological but also architectural and business aspects, or even regulation, the 5G slicing shows a novel attack surface but also great opportunities to deliver the relevant level of cybersecurity.
The following sections will briefly highlight main issues and specific potential directions.
Figure 1: Overall slice vision
“What’s in my Slice”?
The 5G slices are Software-based and as such, inherit among others from SDN and NFV security issues and solutions. Many threat Intelligence aspects are already addressed in the literature including comprehensive survey [10] or, for instance for SDN-NFV components, available as Common Vulnerabilities and Exposure (CVE) list.
As described in [5] 5G relies on a set of security functions which have to be instantiated on a per slice basis. Security should be tuned as per tenant/vertical policies for a given slice which implies in turn to manage/duplicate the security functions on logical slices. A user may access different slices for different services, but the confidentiality, integrity and availability has to be preserved for any slice. Most of the issues pointed here may be summarized as isolation issues. The potential attacks can affect tenant services by targeting user data but attention should be paid to the control exchanges (e.g negotiations of Slice as a Service, templates etc...).
When considering knowledge of slice assets and its consequences in terms of security issues, a specific problem occurs by nature as the slices are both:
- an abstraction/composition of the actual systems and services delivered by third parties and,
- flexible, dynamic or even adaptive to satisfy the varying needs through multi-party complex business environment
The 5G is actually disruptive and the security issues raised by 5G slicing will remain work in progress for some time. Compensating the new threats and issues, security should inherit from the best 5G paradigms. Some beneficial 5G aspects applied to security are presented below.
Software Defined Security: Slice Protection Deployments
5G slices is a new way to virtualize an infrastructure for tenants with dynamic software defined provisioning technologies and service aggregation rather than system integration approach. Deployment, orchestration, chaining of (virtualized) protection functions becomes by analogy a software defined security concept.
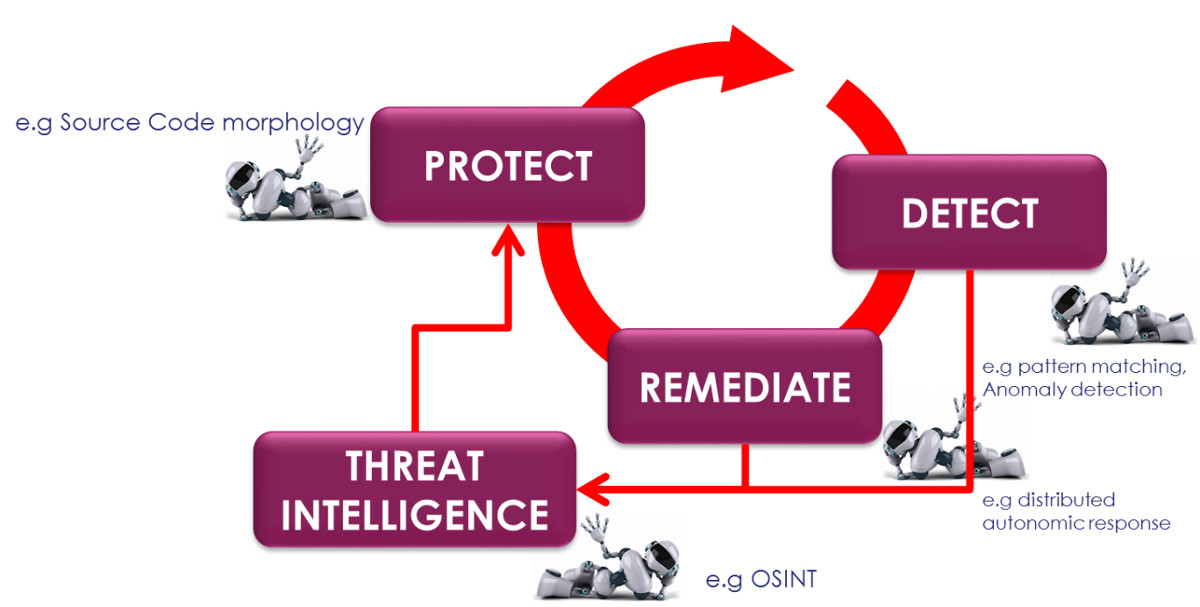
This provides a great opportunity, allowing fine grain policies, Artificial Intelligence-based smart algorithms (security phases illustrated in Fig. 2), etc... The end-to-end security is thus resulting from the diversity of stakeholders involved in the provision and usage of the slices. As an immediate consequence, horizontal (end-to-end), vertical (infrastructure provider vs. tenants), multilateral (security-as-a-service, vertical services) coordination/composition of security becomes a challenge. Beyond technical aspects, the liability distribution is expected to have a major impact on the slice security operations.
Nevertheless, the control and flexibility of the software defined security is an enabler for innovative slice defense strategy. Among 5G slicing related security concepts, two categories are emerging, in both cases using the ability to automate the manipulation of the system morphology:
- Micro-segmentation [11] can provide fine grain isolation, specific access control & security policies.
- Deception, overcoming historical honeypots, is assuming that advanced (often unknown/zero days) attacks will be defeated by deceiving the attackers with enabled dynamic/smart proactive security.
Security-as-a-Service should be a companion to 5G Slices. Not all tenants will have internal up-to-date expertise available to manage all security aspects. It is thus expected that a wide range of security will be delivered by managed security service providers. As an example, Identity and Access Management (IAM) as a Service will be key to distribute and control respective authorities and access across multiple 5G systems stakeholders. Many other security aspects (Key Management, Intrusion detection...) will be handled this way participating to the slice security.
Figure 2: Enabled Smart Slice security with Artificial Intelligence
Monitoring, Attack Detection and Remediation
As aforementioned, knowledge of slice security conditions is not straightforward considering the multiplicity of authority perimeters and the complexity of dependencies between sub-systems, services etc... Slice security mandates continuous monitoring tracking events or anomalies end-to-end. This dynamic assessment may require both specific advanced tools but will have to face the boundaries of respective stakeholder perimeters. Monitoring or reporting security data is an open field. A particular case is the response to incident which basically require sharing of information from detection towards tenants or adjacent party interconnected.
As for protection deployment, detection and remediation are the purpose of smart AI-based strategies that may be applied on a per-tenant basis. Each and every tenant may for instance deploy its own probes for attack detection across his slice, in addition to some reporting delivered by the providers. Specific remediation strategies may then apply relying on specific critical asset knowledge on tenant side. One can obviously anticipate some remaining challenges with respect to the actual isolation (inter-dependencies) of the slices from other slice/underlying infrastructure or the need of signaling/exchanges between the actors. It should be also noticed that those exchanges are subject to potential attacks and should be secured (may be a specific dedicated “control and management” slice.)
Conclusion
The promising 5G Network Slicing won’t become a reality without embracing security concerns. Some of the specific weaknesses are resulting more from architectural patterns than basic technologies. The opportunity to transform security into smart, dynamic, accurate, fine grain strategies applications concomitantly with 5G evolution is both promising and needed.
References
[1] GENI, Global Environment for Network Innovation, Key GENI concepts, http://groups.geni.net/geni/wiki/GENIConcepts
[2] IETF, RFC 5212, Requirements for GMPLS-Based Multi-Region and Multi-Layer Networks (MRN/MLN)
[3] NGMN Alliance: "Description of Network Slicing Concept", Version 1.0, January 2016.
[4] NGMN Alliance: "5G Security Recommendations Package #2: Network Slicing” Version 1.0, April 2016.
[5] 3GPP TS 23.501, “System Architecture for the 5G System”,
[6] 3GPP TS 23.502, “Procedures for the 5G System”
[7] 3GPP TR 33.899, “Study on the security aspects of the next generation system”
[8] 3GPP TS 33.501, “Security architecture and procedures for 5G System”
[9] 5G PPP Phase 1 Security Landscape, https://5g-ppp.eu/white-papers/
[10] Scott-Hayward, S., Natarajan, S., & Sezer, S. (2016). A Survey of Security in Software Defined Networks, IEEE Communications Surveys and Tutorials
[11] Olli Mämmelä, Jouni Hiltunen, Jani Suomalainen, Kimmo Ahola, Petteri Mannersalo, Janne Vehkaperä, “Towards Micro-Segmentation in 5G Network Security”. EuCNC 2016
 Emmanuel Dotaro is the director of ICT and Security labs at Thales Secure Communications and Information Systems. He joined Thales in 2009 as director of innovation for C4I systems. Beside his current research and innovation management activity he is involved in various National and European ICT and Cybersecurity initiatives. He serves in both 5G-IA and ECSO PPP’s associations boards as well as various Technical Committees or clusters of the digital ecosystem. His current areas of interests are network virtualization and softwarization, cloud brokering, security as a service, security policies enforcement in 5G and IoT systems as well as certification, detection, remediation related security topics.
Emmanuel Dotaro is the director of ICT and Security labs at Thales Secure Communications and Information Systems. He joined Thales in 2009 as director of innovation for C4I systems. Beside his current research and innovation management activity he is involved in various National and European ICT and Cybersecurity initiatives. He serves in both 5G-IA and ECSO PPP’s associations boards as well as various Technical Committees or clusters of the digital ecosystem. His current areas of interests are network virtualization and softwarization, cloud brokering, security as a service, security policies enforcement in 5G and IoT systems as well as certification, detection, remediation related security topics.
Editor:
 Marie-Paule Odini is Distinguished Technologist in HPE with over 25 years of telecom experience. She is focusing on customer innovation and emerging trends in the communication industry including NFV, SDN, IoT, big data and 5G and leads technology discussions and solution roadmaps towards 5G inside HPE. She is also involved in industry forums and standard organization such as ETSI NFV Vice Chair, IEEE SDN Chair and Editorial board member, 5G Americas co-author of Network Slicing and V2X white paper and more recently as co-chair of TIP (Telecom Infra Project) new E2E network slicing project.
Marie-Paule Odini is Distinguished Technologist in HPE with over 25 years of telecom experience. She is focusing on customer innovation and emerging trends in the communication industry including NFV, SDN, IoT, big data and 5G and leads technology discussions and solution roadmaps towards 5G inside HPE. She is also involved in industry forums and standard organization such as ETSI NFV Vice Chair, IEEE SDN Chair and Editorial board member, 5G Americas co-author of Network Slicing and V2X white paper and more recently as co-chair of TIP (Telecom Infra Project) new E2E network slicing project.
Subscribe to IEEE Softwarization
Join our free SDN Technical Community and receive IEEE Softwarization.
Article Contributions Welcomed
Download IEEE Softwarization Editorial Guidelines for Authors (PDF, 122 KB)
If you wish to have an article considered for publication, please contact the Managing Editor at sdn-editor@ieee.org.
Past Issues
IEEE Softwarization Editorial Board
Laurent Ciavaglia, Editor-in-Chief
Mohamed Faten Zhani, Managing Editor
TBD, Deputy Managing Editor
Syed Hassan Ahmed
Dr. J. Amudhavel
Francesco Benedetto
Korhan Cengiz
Noel Crespi
Neil Davies
Eliezer Dekel
Eileen Healy
Chris Hrivnak
Atta ur Rehman Khan
Marie-Paule Odini
Shashikant Patil
Kostas Pentikousis
Luca Prete
Muhammad Maaz Rehan
Mubashir Rehmani
Stefano Salsano
Elio Salvadori
Nadir Shah
Alexandros Stavdas
Jose Verger